I know you may rest assured about the formidability of your IT systems. Just try this D.U.D.E thing tomorrow morning.
- Have any questions?
- info@synersoft.in

Helping MSMEs eradicate at least ten hazards of Data Loss
September 30, 2022
Synerology 2022 – Kumbhalgarh
November 25, 2022Devil’s Advocate DUDE thing Series
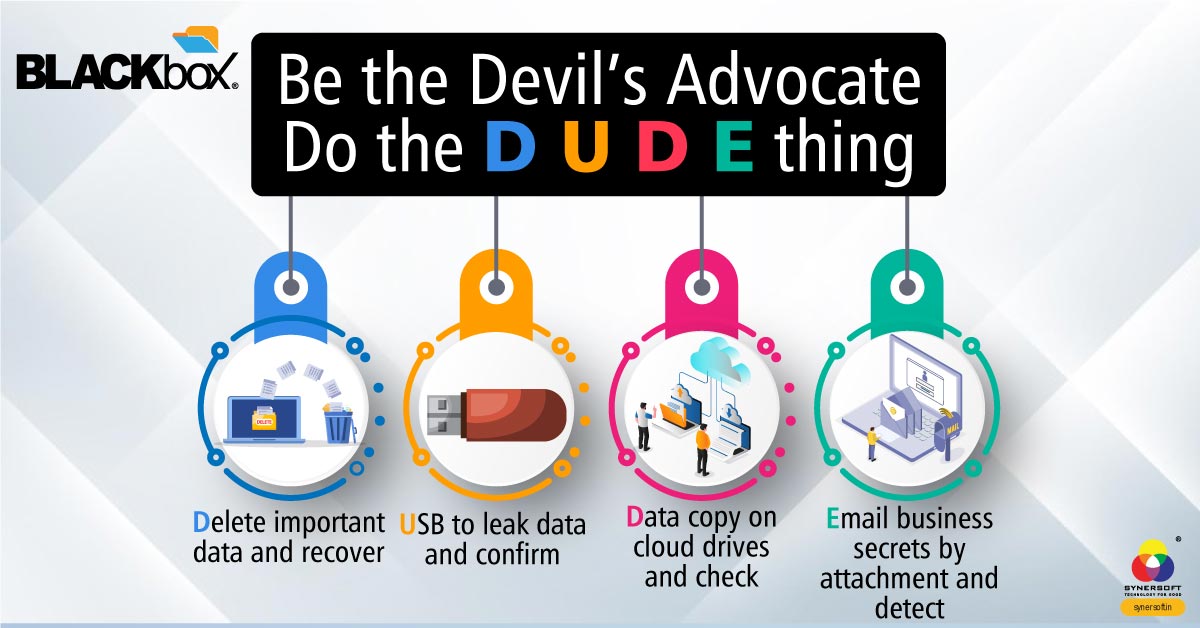

D for Delete Critical Data
Go to a network folder, or access the desktop of a user’s system and shift + delete + yes, some critical files.
Then try to get the same data back in the same form at the time of deletion.
I am sure there is a 99 percent chance you will not get the data in the same format. Your act of being a devil’s advocate will bring you to reality ground.
That’s not all. Try to check if your act of deleting the files was logged somewhere. You would have needed it if a user had deleted a critical file intentionally without letting anyone know.
If you cannot recover the deleted data and know who deleted it, let me tell you, you are not in an extraordinary situation. What if your users intentionally deleted data from the network or their computers, and your organization is chasing a project deadline, tender timeline, or last moment customer submission?
There needs to be better control of the situation. In no circumstances should you be put in such a vulnerable situation where you can’t recover deleted data or can’t find out who intentionally deleted your data.

U for USB Confidential Data
Go to your server or the user’s system, insert a USB drive or connect mobile by cable and copy critical data. If you are successful in doing it, you are in a fix. There are three scenarios to explain this.
No Security
You may not have any security policy to control USB ports on users’ computers. You must have control over USB misuse.
Business Requirement
The user is granted USB access because they have to use a digital signature dongle, software license dongle, or camera over the USB as a part of their job to file statutory returns or inward data or validate dongle-based software licenses. All these business requirements do not justify granting uncontrolled USB access to these users. You must have control over the USB port such that digital signatures, license dongles, and data-inward operation works without granting rights to copy data outward on the USB port.
Trust Factor
The user is loyal and trusted with the requirement of taking critical data out on USB for genuine purposes. What if the user has outwarded the data, which they are not supposed to? You must have a reporting system which documents and intimates the details of what data is outwarded.

D for Data Upload on Cloud Drives
Go to any user’s laptop, connect to the Internet by mobile hotspot, and upload critical data on google drive, Dropbox, or any cloud drive. If you can do so, the users can also do so. It is not a piece of good news. The users might argue that he needs access to such cloud drives because they have to download the data exchanged by the customers or for other reasons. A good IT policy is about allowing users to download data from cloud drives and preventing them from uploading data on the cloud drive.

E for Email Attachment Misuse
Go to any user’s laptop or computer, open email and send critical confidential data to a competitor or personal mail id. If you can do it without anyone knowing about it, the users can also. You need to define email policy and have systems to enforce the email vigilance policy.
This D.U.D.E. thing will reflect the fragility or formidability of your IT systems with a view to data loss, leakage, or theft. Our product BLACKbox is designed to deal with most of these situations and help MSMEs to focus on their business rather than worrying about these devil’s favourite DUDE things.