This short five-minute reader will help you understand how BLACKbox can solve some critical business problems. We are in this journey together and would love to assist your organization.
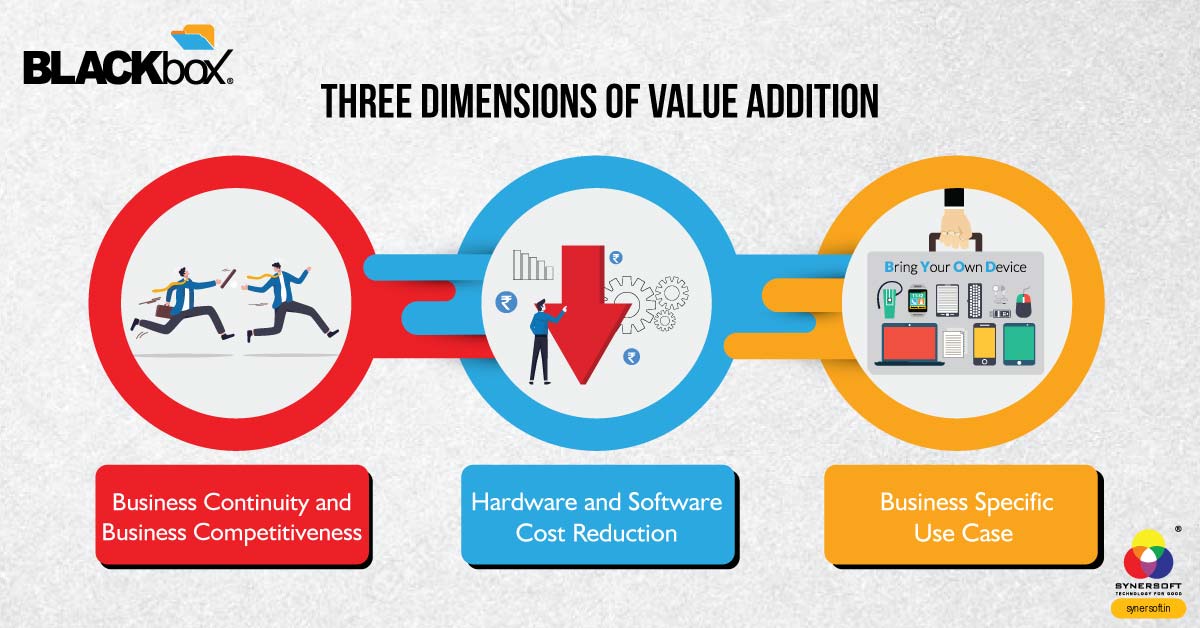
1. Business Continuity and Business Competition
Data loss can have serious impact on Business Continuity and Data Theft can lead to exploitation by competitors. BLACKbox ensures Business Continuity in event of accidental or intentional deletion, ransomware attack, disaster, and hardware failure. BLACKbox prevents competitive exploitation by protecting data from being copied using the USB port, sending data as email attachments, sending emails with blind carbon copy (BCC), and online cloud storage drives such as Dropbox. BLACKbox complies with stringent data protection and information security standards.
2. Hardware and Software Cost Reduction
BLACKbox Solutions serve as a single hardware single endpoint solution which makes it simple to manage and cost effective. It is an all-in-one product which can replace multiple IT infrastructure components like File Server, Domain Controller, Storage Device, End Point Security, Backup Agent, Email Vigilance System, Internet Proxy Server, VPN Server, Remote Desktop Server, Application Virtualization Server, and Cloud Backup. It saves significant licensing cost in terms of server license, client access licenses, and RDP CAL licenses.
3. Business Specific Use Cases
BLACKbox serves as a reliable solution for various use cases like: Fast and secured access to data and applications during Work from Home (WFH), data leakage prevention on BYOD user (Bring Your Own Device), Data recovery after accidental deletion of data, data recovery after ransomware attack, data restoration after disaster or hardware crash, vigilance of emails, productivity monitoring by screen capture, Deduplication of the data, autocratic centralization, and many more use cases.
For a business owner, it serves as a key data loss, leakage, and theft prevention solution to maintain business continuity and avoid competitive weakness.
For an IT professional it serves as a powerful and cost-effective hardware plus software tool which can replace an integration of discrete IT components like File Server, Domain Controller, Storage Device, End Point Security, Backup Agent, Email Vigilance System, Internet Proxy Server, VPN Server, Remote Desktop Server, Application Virtualization Server, and Cloud Backup.
For an enterprise, It proves itself worthy and dependable for a variety of use cases.
We are sure that this article is insightful and will assist you to make a right choice.