- Have any questions?
- info@synersoft.in

Launch Announcement – UNITED SMEs
January 22, 2021
Tesla could detect and react, can you?
February 3, 2021Beware of You v/s You Fraud
We draw your attention to the recently launched cyber-attack impacting millions of unsuspecting email users.
Leaders at your organization must know about it. At first glance, it looks like a routine email from a colleague. It is not. It is notable that though it surfaced in the last two weeks and still is escaping the smartest of antispam features.
The modus operandi is brilliant. The user gets an email from IT Team or Accounts Team with an actionable link. As one clicks on the link, the attack starts, and in no time, it spreads across network users, network drives, and servers.
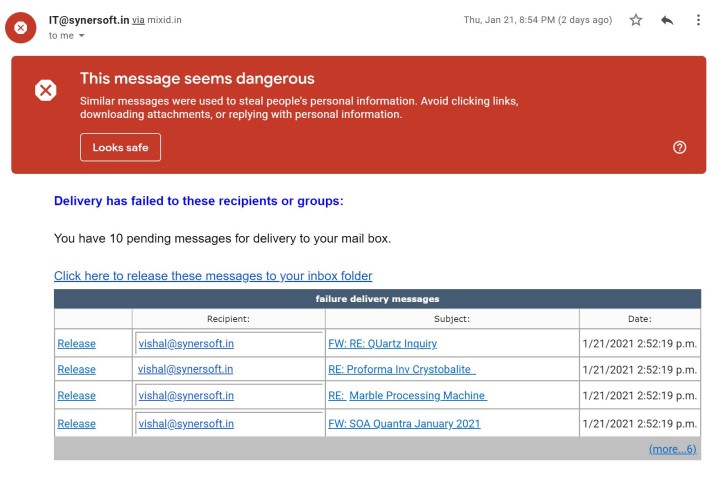
It impacts most email servers that have excluded their emails originating from their own domain from the antispam filters. Below is a sample of such a fraudulent email as captured by our Research Team.
You can immediately check the following points and set them right if required.
- Please check the SPF record in your DNS zone file. If it is not there, add it.
- Please generate and add DKIM TXT records in your DNS zone file. If it is not there, add it.
- Please remove any rules you have created in your antispam filters, excluding the emails having sender email id as your company’s id.
- Check PTR and Reverse Lookup entries in DNS Zone Files.
- Advise all the users not to open such emails.
- Make sure that antivirus is updated on every computer system.
We can help. This 2021, we are back with that complimentary Reality Check. We can help you assess the possibility of such vulnerability at your organization, how you can use specific tools like vault and workspace to maintain your business continuity in an unfortunate event of such a ransomware attack.





